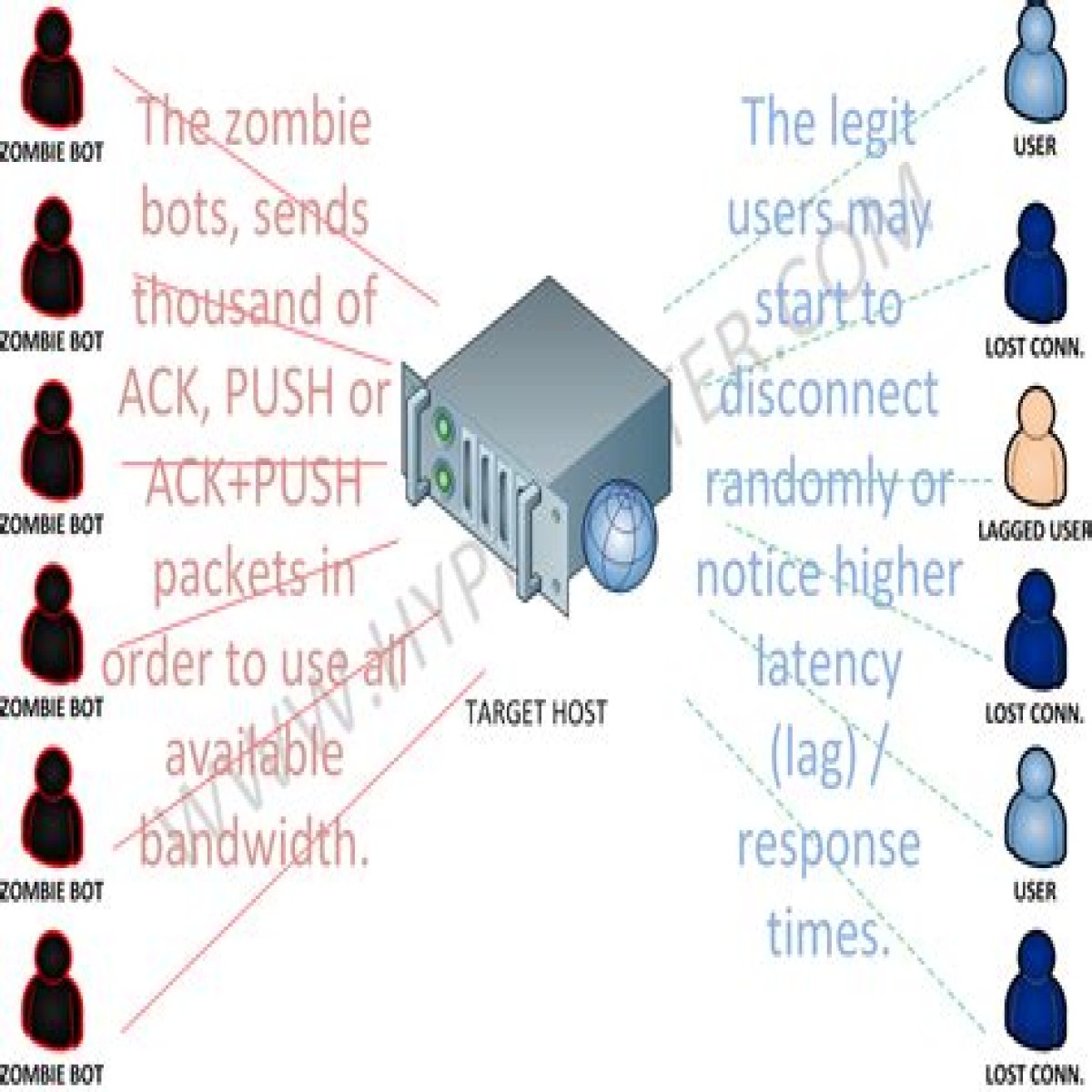
What is a push ACK Attack?
In an ACK DDoS attack (or ACK-PUSH Flood), attackers send spoofed ACK (or ACK-PUSH) packets at very high packet rates that fail to belong to any current session within the firewall’s state-table and/or server’s connection list.
What is a PSH attack?
An PSH flood is a DDoS attack designed to disrupt network activity by saturating bandwidth and resources on stateful devices in its path. By continuously sending PSH packets towards a target, stateful defenses can go down (In some cases into a fail open mode).
What is in an ACK?
An ACK packet is any TCP packet that acknowledges receiving a message or series of packets. Technically, an ACK packet is a TCP packet with the “ACK” flag set in the header. ACK packets are part of the TCP handshake, a series of three steps that start a conversation between any two connected devices on the Internet.
What is DoS attack ICMP flood?
An Internet Control Message Protocol (ICMP) flood DDoS attack, also known as a Ping flood attack, is a common Denial-of-Service (DoS) attack in which an attacker attempts to overwhelm a targeted device with ICMP echo-requests (pings).
What does ACK mean in networking?
(ACKnowledgment code) The communications code sent from a receiving station to a transmitting station to indicate that it is ready to accept data. It is also used to acknowledge the error-free receipt of transmitted data.
What is DOS attack ACK scan?
The DOS attack: ack scan basically informs you that the firewall is working properly. [DOS Attack: ACK/SYN SCAN] from “ip address,” port “port number,” “day,” “date.” Example: [DOS ATTACK: SYN/ACK SCAN] from 34.66. 232.251, port 95, Sunday, December 25, 2022.
What Is PSH ACK in Wireshark?
The ACK indicates that a host is acknowledging having received some data, and the PSH,ACK indicates the host is acknowledging receipt of some previous data and also transmitting some more data.
Is ACK flood DOS or DDoS?
ACK floods are layer 4 (transport layer) DDoS attacks. Learn about layer 4 and the OSI model.
What is an ACK storm?
An ACK storm occurs when an attacker first starts to take over a session and sends spoofed packets. The server does this by sending SYN and ACK packets, which the other system replies to with its own SYN and ACK packets. The result is an ACK storm.
Why is an ACK used?
In data networking, telecommunications, and computer buses, an acknowledgment (ACK) is a signal that is passed between communicating processes, computers, or devices to signify acknowledgment, or receipt of message, as part of a communications protocol.